Network Architecture
Here are the various building blocks required to create a STAGE / Virtual SmartPanel system and how they are interconnected. These network diagrams will have to be adapted to your actual network architecture, including the use of STUN and TURN servers when there is a need to send signals through firewalls.
See chapter Riedel STAGE™ & Virtual SmartPanel® – How to Implement STUN and TURN and chapter Network Considerations.
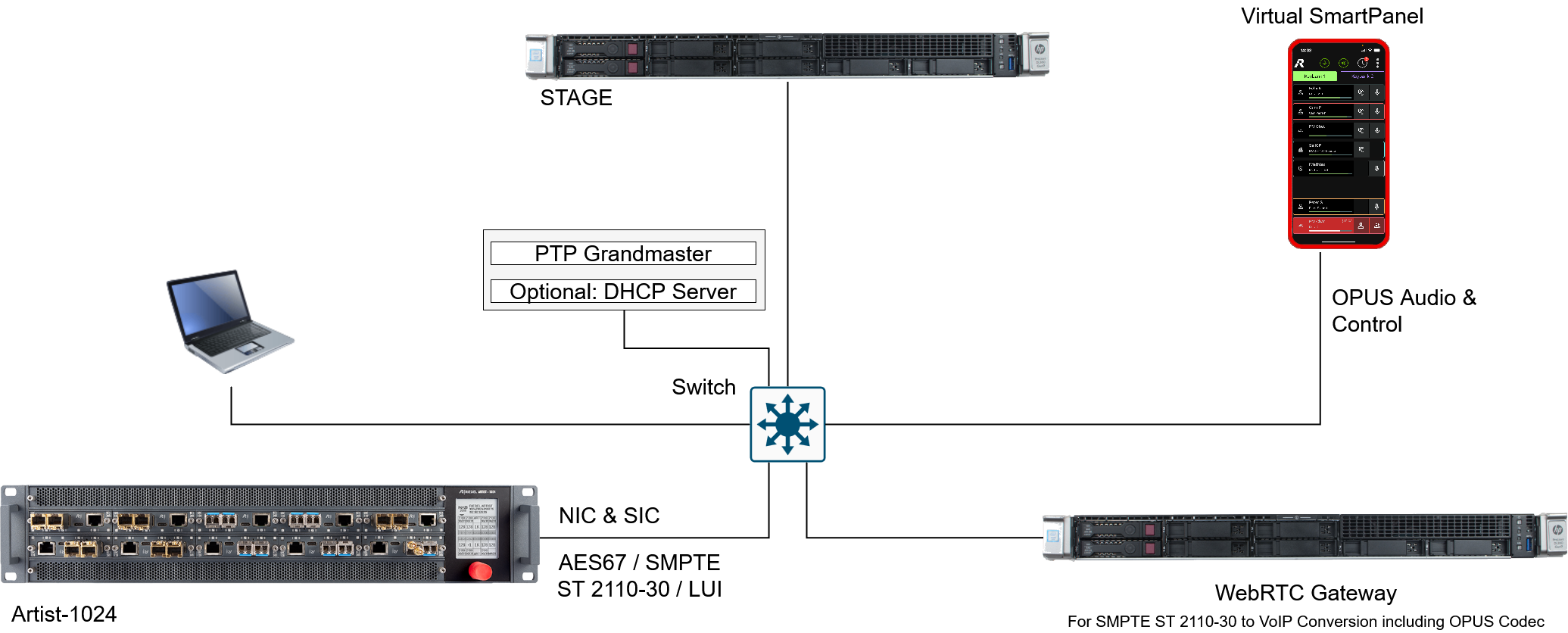
Basic System
The simplest system that can be built is one involving a single STAGE server, a single Artist-1024, a single WebRTC Gateway server and a single Virtual SmartPanel all connected onto the same network infrastructure used for both Control and Media communications.
In this scenario, there is no redundant connectivity nor any clusters, which means failure of one of these elements may bring down the entire system.
Basic System
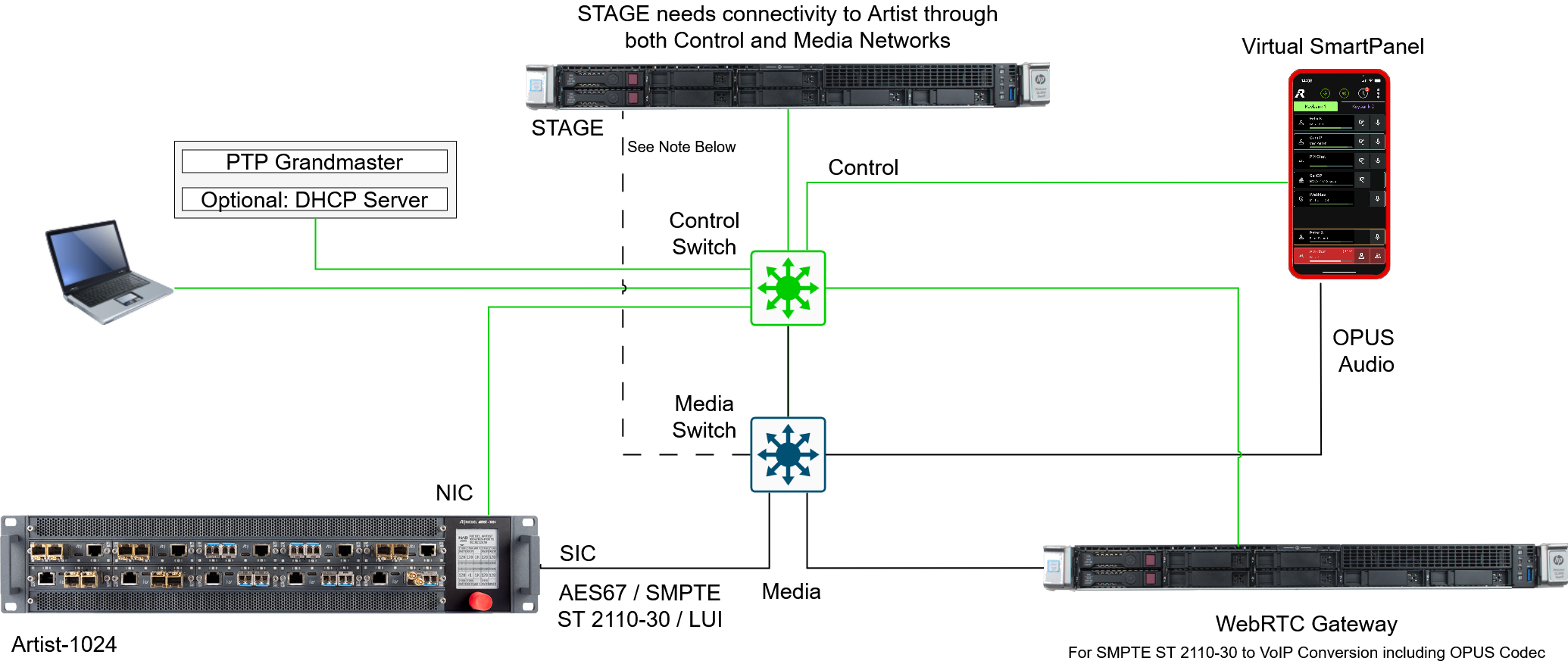
Split Media and Control Networks
Splitting the Control network from the Media network can ensure that the network bandwidth requirements for the Media network are always being met. In this application, STAGE needs connectivity to Artist through both the Control and Media networks.
Split Media and Control Networks
STAGE nodes may need Static Routes to be configured when media interfaces are not on the same subnet as the Artist SIC ports. For example, when the media network is segmented into L3 parts with say PIM routing in between L3 parts. Without static routes, STAGE nodes would route the traffic through the default gateway which typically is the control interface, that would have no IP connectivity with the Artist SIC ports.
See also chapter Network Considerations #In-band vs. Out-of-Band Management.
To simplify the management of IP addresses and other server-related settings, the 3rd party software Cockpit project can be used, which is installed on the Cluster Nodes. Further information can be found in the separate user manual: RSM > Preparations #Cockpit-Project.
Using External Nodes when STAGE is Connected to the World Wide Web
When STAGE is exposed to the Internet, to support the Virtual SmartPanel offsite for example, an advanced network architecture is used to protect STAGE's main cluster running on an internal network from unauthorized access by using External Nodes. See the diagrams in chapter Default Ports.
STAGE External Nodes have the following qualities:
Typically runs in De-Militarized Zone (DMZ) and provide a point of presence. The external nodes in the DMZ are reachable through a separate IP Address and not through VRRP (as this is routed in a separate VLAN).
Does not host configuration database.
Hosts the STAGE UI and can be used for external authentication.
Is used by Users outside of core network to access STAGE UI.
The goal is to Authenticate External users through Keycloak and possible external IdPs before Traffic is routed inside the internal network. No Data flows between external clients and STAGE core services before Authentication.
The external nodes only run the necessary services to allow access by external clients. All sensitive data runs inside the internal network.
The STAGE Suites redirection URL (as Cluster FQDN) is the same for all nodes, meaning that the FQDN needs to be resolvable from internal and external.
To install a STAGE External node, use RSM. It uses the same STAGE suite file, however, in RSM you need to identify the STAGE node as an external one (by setting the External Node installation option in the RSM for that node).